Privacy by Design puts privacy at the core of every product, service, and system from the earliest stages of development, guiding decisions about data collection, storage, and user interactions. In today’s data-driven world, reacting to privacy incidents after the fact is no longer sufficient, so teams embed protective measures from the outset to minimize risk and preserve data privacy and user trust. Privacy by Design invites teams to bake privacy into architecture, features, and business processes from day one, ensuring default protections, consent mechanisms, and governance practices are integral rather than retrofitted. The approach rests on well-established privacy by design principles that guide design decisions, technical choices, and governance structures, including proactive risk identification, end-to-end security, transparency, and a commitment to user control across teams and throughout the project lifecycle. Adopting this mindset helps organizations reduce risk, improve trust in technology, and align with evolving regulatory expectations while delivering meaningful privacy-preserving features at every stage of development, measurement, and iteration.
An equally important lens is to view privacy as a foundational design principle, sometimes described as data protection by design or a privacy-first architecture. From governance to product development, teams should bake safeguards into requirements, choosing minimal data collection, robust access controls, and transparent consent workflows. This approach complements strong security by design, ensuring that encryption, authentication, and monitoring accompany data as it moves through systems. By integrating privacy considerations with privacy governance metrics, regulatory readiness, and ongoing risk assessments, organizations can build trust in technology while meeting stakeholder expectations. Ultimately, the conversation shifts from reactive fixes to proactive protection, aligning product strategy with user rights, data minimization, and responsible data sharing.
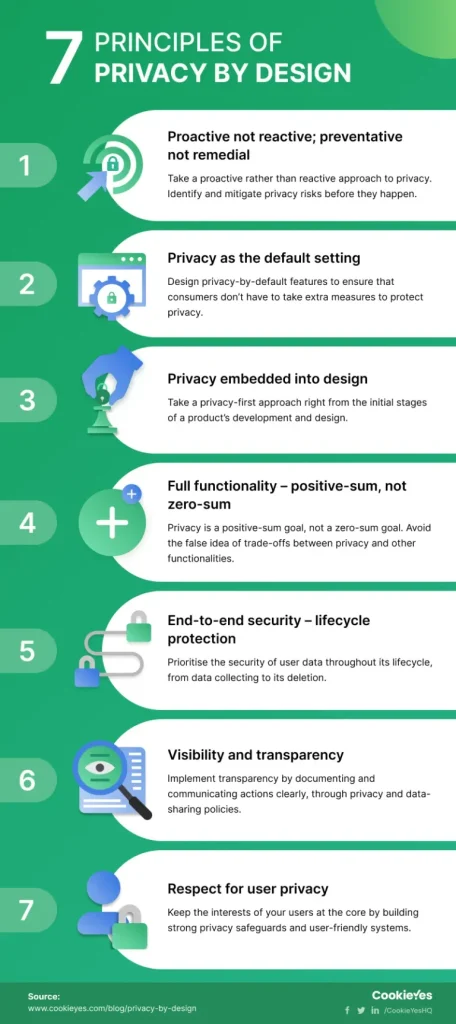
Privacy by Design: From Concept to Core Architecture
Privacy by Design is not a bolt-on feature; it is a philosophy that threads privacy into the core architecture from the earliest design stages. It aligns with the seven foundational principles, guiding design decisions, technical choices, and governance structures to put privacy at the center of product development. Emphasizing proactive risk management, default privacy, and privacy embedded into design helps ensure data privacy is a consideration at every step rather than an afterthought.
Operationalizing Privacy by Design means mapping data flows, conducting data minimization, and integrating privacy controls into system architecture. Employing privacy-enhancing technologies such as pseudonymization and encryption, along with robust access controls, reduces exposure of personal data and strengthens end-to-end protection. This approach also supports privacy governance by embedding privacy into decision points across product teams, from ideation to deployment, and aligns with broader trust in technology goals.
Embedding Default Privacy: How to Make Privacy the Default Setting
Making privacy the default requires configuring systems so personal data is automatically protected in any environment, minimizing the need for user action. By adhering to privacy by design principles, teams practice data minimization, set consent and opt-out options by default, and ensure sensitive data is guarded from the outset. This shift reduces configuration errors and enhances data privacy right at the source.
Default privacy supports regulatory alignment and user confidence. With privacy enabled by default, organisations can demonstrate commitment to data protection, streamline privacy governance activities, and deliver a more secure user experience. The result is stronger trust in technology, lower risk of violations, and a clearer pathway for ongoing privacy improvements.
Governance and Accountability: Building a Privacy Governance Framework
A robust privacy governance framework defines roles, responsibilities, and processes to monitor privacy risk across the product lifecycle. Regular privacy impact assessments, ongoing monitoring of controls, and transparent reporting are essential components. Establishing these practices helps ensure that privacy considerations are embedded in everyday decisions rather than treated as a separate compliance activity.
A cross-functional team—product, engineering, legal, security, and data science—ensures privacy governance is represented at every decision point. Clear data retention policies, access controls, and careful third-party data sharing discussions become routine. This integrated approach supports accountability for privacy risk and reinforces data privacy across the organization.
Security by Design as a Companion to Privacy: Protecting Data Across the Lifecycle
Security by design complements Privacy by Design by ensuring data protection travels with information from collection to deletion. Technical controls such as zero trust architectures, encryption at rest and in transit, secure development lifecycles, and regular vulnerability management are essential. When privacy and security are designed together, the protection is stronger and more cohesive.
A combined focus on privacy and security reduces the likelihood of data breaches and regulatory penalties while boosting user confidence. By integrating security by design with privacy principles, organizations demonstrate a holistic commitment to data protection, supporting trust in technology and measurable improvements in risk posture.
Data Minimization and Data Flow Mapping: Reducing the Data Footprint for Data Privacy
Understanding data flows through data mapping and adopting data minimization by default are foundational steps to protect data privacy. Identifying what data is collected, why it is collected, where it travels, who has access, and how long it is retained helps teams remove unnecessary data and apply privacy by design principles across the architecture. This practice also supports governance by keeping data inventories current and auditable.
As data moves across systems and vendors, careful management of sharing and retention becomes critical. Combining data minimization with anonymization or pseudonymization where feasible helps preserve utility while reducing exposure. Strong privacy controls and clear data subject rights workflows ensure compliance and reinforce trust in technology.
Trust in Technology: How Transparent Privacy Practices Build User Confidence
Trust in technology grows when users understand how their data is collected, used, and protected. Transparent data practices, clear explanations of data handling, and straightforward consent mechanisms empower users and align with privacy governance goals. Consistent privacy communications foster an ongoing relationship where users feel their rights are respected.
Beyond compliance, measurable privacy outcomes and reliable performance reinforce trust. When organizations demonstrate accountability through regular reporting, audits, and responsive data subject rights processes, users are more likely to engage, transact, and share data when appropriate. This trust in technology translates into competitive advantage and long-term resilience in privacy-focused markets.
Frequently Asked Questions
What is Privacy by Design and why is it essential for data privacy and trust in technology?
Privacy by Design is a proactive framework that embeds privacy into the core of products from the start. It enhances data privacy and builds trust in technology by applying the seven foundational principles—such as default privacy, end‑to‑end security, and transparency—across product and governance decisions.
How do privacy by design principles support privacy governance and security by design?
Privacy by design principles provide a structured approach—proactive risk management, privacy as default, and privacy embedded into design—supported by clear privacy governance. They also integrate security by design controls like encryption, zero trust, and regular audits to protect data.
What practical steps can teams take to implement Privacy by Design during product development?
In practice, map data flows to understand journeys; apply data minimization; embed privacy controls into architecture (default settings, consent, encryption); adopt privacy engineering; and establish cross‑functional privacy governance with product, legal, security, and data science teams.
How does data privacy regulation align with Privacy by Design and privacy governance?
Privacy by Design helps meet GDPR, CCPA, and other laws by integrating privacy impact assessments, data maps, and retention policies into privacy governance, reducing regulatory risk while delivering business value.
How can organizations maintain full functionality without sacrificing privacy under Privacy by Design?
By pursuing solutions that preserve core functionality while protecting data, leveraging privacy‑enhancing technologies, and redesigning processes so privacy is foundational—not a tradeoff.
What is the relationship between security by design and Privacy by Design in protecting data throughout its lifecycle?
They are complementary: security by design guards data in transit and at rest, while privacy by design guides data collection, retention, and user rights; together they strengthen data privacy and trust in technology.
| Aspect | Key Idea |
|---|---|
| Proactive not reactive | Anticipate privacy risks before they occur and act to stop them. |
| Privacy as the default | Personal data is automatically protected in any given environment without requiring users to take action. |
| Privacy embedded into design | Privacy is integral to the core architecture, not tacked on as an afterthought. |
| Full functionality, not a tradeoff | Seek solutions that preserve privacy while maintaining core functionality and user experience. |
| End to end security | Data safeguards travel with information from collection to deletion, including encryption, access controls, and robust authentication. |
| Visibility and transparency | All privacy practices are open to verification, with clear communication to users about data handling. |
| Respect for user privacy | Privacy decisions reflect user preferences and rights, with mechanisms for consent, control, and redress. |
| Data governance and lifecycle integration | Data flow mapping, data minimization, retention policies, and privacy controls embedded across the product lifecycle. |
| Governance and cross-functional teams | A privacy governance model with clear roles, regular privacy impact assessments, and ongoing monitoring; cross‑functional teams ensure privacy at every decision point. |
Summary
Privacy by Design is a foundational approach for modern technology development that centers privacy from the earliest stages of product creation. It emphasizes embedding privacy into architecture, workflows, and governance rather than adding it after the fact. By translating the principles into concrete actions across ideation, design, development, and operations, organizations can reduce risk, build trust, and better align with evolving regulatory expectations. In the era of AI and connected devices, Privacy by Design guides purpose limitation, data minimization, and transparent governance while enabling responsible innovation. Strong privacy governance, data stewardship, and cross‑functional collaboration turn privacy into a competitive differentiator and a pathway toward a more trustworthy digital future.